“ Alert!! Your system is compromised! ” It is not concerned until there is a loss in the data or private files. Why wait so long? Maybe this interests you if I say this article says about one of the simplest ways to protect your privacy and keep them secured. Track down before it gets out of hands. Let’s get started!
Any illegal usage of these technique might be punishable. This is just for the purpose of knowledge.
Again, have you ever received a token, that can be at shows, restaurants, hospitals, etc? Why are they given? To identify? Yes, mostly they are unique and can be used to identify, keeping aside the discount tokens!! So, canary tokens are similar to this concept. In the earlier days, Canaries were used in the coal mines to identify the levels of Carbon monoxide that is toxic to humans. Due to the high metabolism and breathing rates of these species, miners led these birds to the dangerous mines to succumb before them. Canary birds are highly sensitive to poisonous gases thereby leaving time for action to the miners.
What these canaries actually doing? Alerting the miners from the poisonous gases. Similarly, canary tokens alert the admins or users from breaches and reduce the time required to identify them. These tokens act as tripwires and take forms of a PDF, URL, Email, Image, or an API. When an intruder or an attacker accesses these types of files, alerts will be fired to the admins, analysts and a security response team can start investigating the trespassing with less loss.
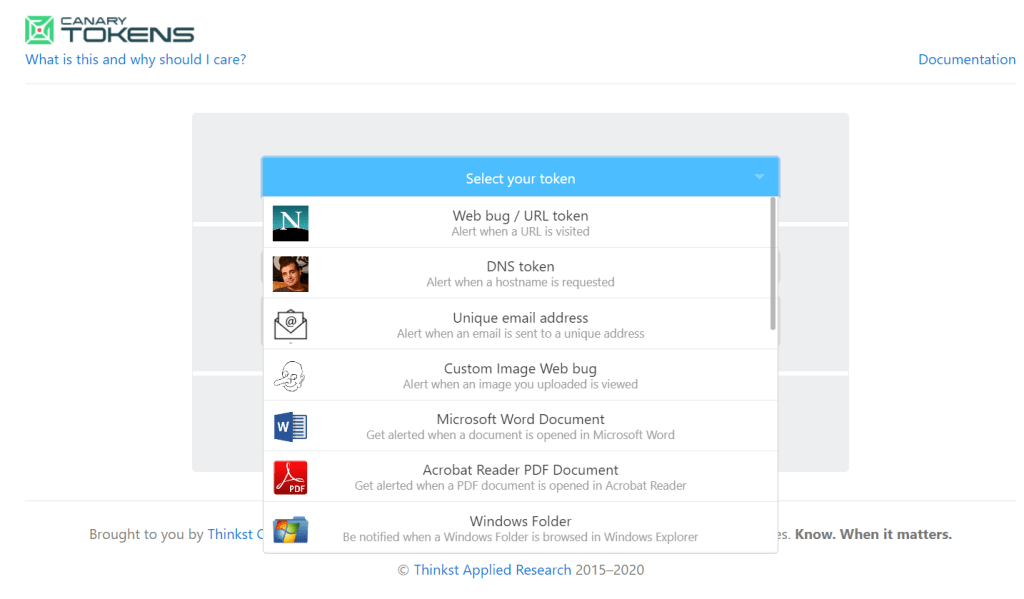
Details of Tokens:
- Web bug/URL Token: This is used as clickable link and can be embedded in mails or at any other media. You will be notified when someone clicks on the link to the given mail. These links are modifiable and can be used to insert as images to prevent a notice.
- DNS Token: Alerts when a given webpage is requested.
- Email Address: When an email is sent to a specific address given, alert will be fired.
- Custom web Image bug: Get notified when the image uploaded on the web is accessed.
- Word document: An alert will be triggered when the document is accessed. This a downloadable document and can be stored where the attack is expected. Use fake data only.
- PDF document: This is similar to the word document.
- Windows Folder: Get notified when the downloaded folder is accessed. This might only work for windows.

Generate Canary Tokens:
A video on Canary Tokens. Language: Hindi. This video explains about the processing of canary tokens briefly.
Don’t go for attackers. Prepare something that interests them so that they show up eventually. Canaries work similarly to honeypots. Honeypot is a computer system that mimics likely target to cybercriminals. The attackers think that the honeypot is a legitimate target and that’s worth their time. These are the fake login credentials or any fake data that are placed in a network so as to be vulnerable to attacks but with no loss. Blue team will be constantly monitoring if these credentials are used to login to the system or the files are downloaded. This baiting can be assisting in tracking the sources of attack.
Note: Avoid using original data in the documents or any other tokens. Fake data is recommended to avoid any potential data loss. Try this at your own risk.
Types of Honeypots:
Email traps or spam traps place a fake email address in a hidden location where only an automated address harvester will be able to find it. Since the address isn’t used for any purpose other than the spam trap, it’s 100% certain that any mail coming to it is spam. All messages which contain the same content as those sent to the spam trap can be automatically blocked, and the source IP of the senders can be added to a blacklist.
A decoy database can be set up to monitor software vulnerabilities and spot attacks exploiting insecure system architecture or using SQL injection, SQL services exploitation, or privilege abuse.
A malware honeypot mimics software apps and APIs to invite malware attacks. The characteristics of the malware can then be analyzed to develop anti-malware software or to close vulnerabilities in the API.
A spider honeypot is intended to trap web crawlers by creating web pages and links only accessible to crawlers. Detecting crawlers can help you learn how to block malicious bots, as well as ad-network crawlers.
By monitoring traffic coming into the honeypot system, you can assess:
- where the cybercriminals are coming from
- the level of threat
- what data or applications they are interested in
- how well your security measures are working to stop cyber attacks
The use of Honeypots and canaries doesn’t protect the systems completely. There could be attacks at different domains than just at honeypots. Also, if the attacker is aware of the honeypot, he might not touch it and make his work done leaving the security team unnoticed. It is not recommended to solely depend on these systems. It is necessary to maintain regular monitoring of systems and vulnerability assessment checks.
Neologism:
- Address Harvester: A harvester is a software designed to parse huge amounts of data. It can process large number of websites for email addresses, login credentials, phone numbers, etc. Account harvesters record login information from the user to gain legal access to his accounts. Hackers use packet sniffing on the network to extract the data. Harvesting is illegal in specific countries. More details!
- Packet sniffing: This is the method used by network professionals to diagnose network issues. Usually, data is transmitted on a network in the form of packets. These packets are encrypted while in transmission. Hackers search for unencrypted packets that carry sensitive information.
- Web crawling: It is a bot commonly used by the search engines to download and index the webpages so that they can be retrieved when searched. By applying a search algorithm to the data collected by web crawlers, search engines are capable of giving relevant responses to the keywords. It is hard to index every webpage by the Internet and can be overlooked. In order to find all the relevant results, a web crawler bot will start from a certain set of known pages and follow the hyperlinks attached to them and the process go on like a spider web. Hence, these bots can also be termed as spider bots.
- Indexing: It is analogous to indexing the topics in a book so that the reader knows where to go for particular content. So as the Internet understands where to look for relevant webpages.